Anthropic made a simple announcement of Model Context Protocol (MCP) in November 2024 via a brief three-minute-read blog. Arguably, since the launch of Open AI and Claude API’s it has created the maximum excitement in the AI/ML development community. Most AI Agents were relying on custom implementations for each application to hook into its required data sources with relevant context, leading to a lot of duplicated effort. It resulted in disparate prompt logic and different methods for accessing and federating tools and data across different teams and companies. MCP enables AI assistants or agents to interact with any compliant data source or tool without the need for custom integrations.
MCP provides a standardized way for Gen AI agents to:
-
- Share contextual information with large language models
-
- Expose data sources, tools, and capabilities with a common connectivity framework
-
- Build composable integrations and workflows
The architecture consists of a client-server model, where the AI application connects to MCP servers (such as tools, databases, APIs, or other resources) through standardized communication primitives and protocols such as JSON-RPC. At Acuvity, we have been strong proponents of MCP since the announcement and enabled several of our customers to adopt it safely.
Security and Safety Concerns
Model Context Protocol (MCP) has immense benefits as it streamlines AI tool integration but it introduces critical security risks that organizations must address before widespread adoption. The primary security concerns raised by application development and security teams include
-
- Shadow Access – Unmonitored MCP clients and servers create data connection points within agentic applications, increasing the attack surface.
-
- Insecure communication and credentials exposure – Many MCP implementations use unencrypted HTTP, exposing credentials and sensitive data to interception, the agents may also inadvertently expose API keys via tool requests and responses.
-
- AuthN/AuthZ Concerns– At the time of writing, the MCP specification lacks built in AuthN/AuthZ support which can result in unauthorized access to endpoints and tokens with excessive permissions having long lived access to critical systems.
-
- Limited Observability – MCP often lacks basic traceability and integration into tools like Grafana, which results in issues in compliance and incident response.
-
- Supply Chain Vulnerabilities – Malicious actors can upload harmful MCP servers to unofficial repositories. Due to the large number of repositories, ransomware can easily be added to the many MCP servers filesystem.
-
- Runtime Exploits – 30% of MCP servers allow unrestricted URL fetching which could result in attacks like Server-Side Request Forgery (SSRF). Indirect prompt injections can increase further as hidden instructions can be embedded in documents, emails, file attachments or API responses.
MCP Security with Acuvity
Acuvity has significantly enhanced our product capabilities to include support for MCP in our comprehensive Gen AI Agentic security module to mitigate concerns that security teams are faced with as their developers rapidly adopt MCP.
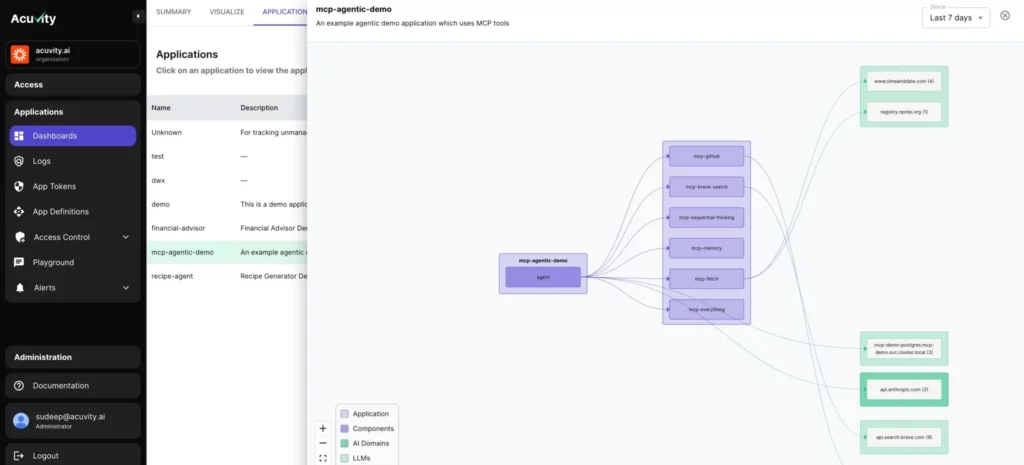
As depicted in the video above the Agentic security module provides complete visibility and runtime protection with SDK, Guardrails embedded in AI Gateways and transparent proxy depending on the environment. Given our scalable security architecture MCP support was added into our framework very easily with new detection capabilities.
For the various security concerns listed above the key components Acuvity has introduced for complete MCP security include –
- sandbox environment that provides a secure, streamlined container runtime designed specifically for MCP servers. This allows running MCP client and server code securely in isolated non root containers with a Read-only filesystem.
- miniaturized transparent proxy seamlessly inserted for streamlining and securing communication between Agents and MCP servers
- Agent authentication, authorization, content analysis, and threat protection for Gen AI pertinent threats MCP clients and servers are susceptible to.
- SBOM Validation for automatic verification of containerized images to prevent compromised deployments.
- Complete observability with Otel integration for OpenTelemetry which allows reporting or rettaching spans from classical OTEL headers, as well as directly from the MCP calls.
- Complete automation for quick deployment into Kubernetes with Helm charts and sensible defaults.
From inception Acuvity was designed with complete visibility, sensitive data protection, content moderation and threat protection, that capability is available for MCP servers with a built-in content analyzer and policer in the miniaturized transparent proxy with following functionality –
- HTTP policer that sends requests to a remote HTTP service to delegate decision
- Rego policer which runs a rego policy file for access control on the request

In addition to indirect prompt injection, jailbreak and other threats for MCP the following threats are relevant and the detections for them are present and constantly being evolved in our Agentic security module –
- Memory Poisoning
- Tool Misuse
- Privilege Compromise
- Resource Overload
- Cascading Hallucination
- Intent Breaking and Goal Manipulation
- Misalignment and Deception
Adopt MCP securely with Acuvity
MCP significantly streamlines the integration of Gen AI agents with external data sources, tools, and applications, offering substantial advantages though it comes with new security risks. Runtime protection with a defensive shield around your MCP based agents provides enterprises the maximum confidence in deploying their apps in production safely.
We, at Acuvity, are excited to enable the Gen AI transformation by providing a free tier for developers and product security engineers to safely and securely adopt MCP.