Runtime Security
Secure Gen AI Applications at Runtime
Acuvity.ai secures your GenAI agents and applications across build, test, and production—empowering safe, scalable innovation. Built for the dynamic nature of GenAI, our runtime security platform offers real-time threat detection, intelligent policy control, and deep visibility into agent behavior. With Shadow AI Discovery, Acuvity uncovers unauthorized tools, risky services, and hidden AI usage—giving you full control and reducing exposure without slowing innovation.
2025 State of
AI Security Report
What the latest data reveals about AI risk, budgets and biggest threats ahead.
Get Your FREE Risk Report
Want to know how risky your AI Services might be? Send us up to five services and we’ll send you back a customized risk report
Shadow AI DiscoveryKey Benefits
Complete Security Across the SDLC
Acuvity secures Gen AI systems across the full software development lifecycle—from development to deployment. We support red teaming, runtime monitoring, and security testing in build, test, and production environments. Integrations with Jenkins, Harness, Snyk, Splunk, XSOAR, and Cribl ensure security works with your existing DevSecOps tooling.
Reduced Attack Surface for Agentic Applications
Gen AI agents introduce new, dynamic attack surfaces. Acuvity inserts security transparently across diverse environments, mitigating OWASP LLM threats like prompt injection, memory poisoning, unauthorized execution, and identity spoofing. We detect behavioral anomalies and policy drift—so you can move fast without opening the door to risk.
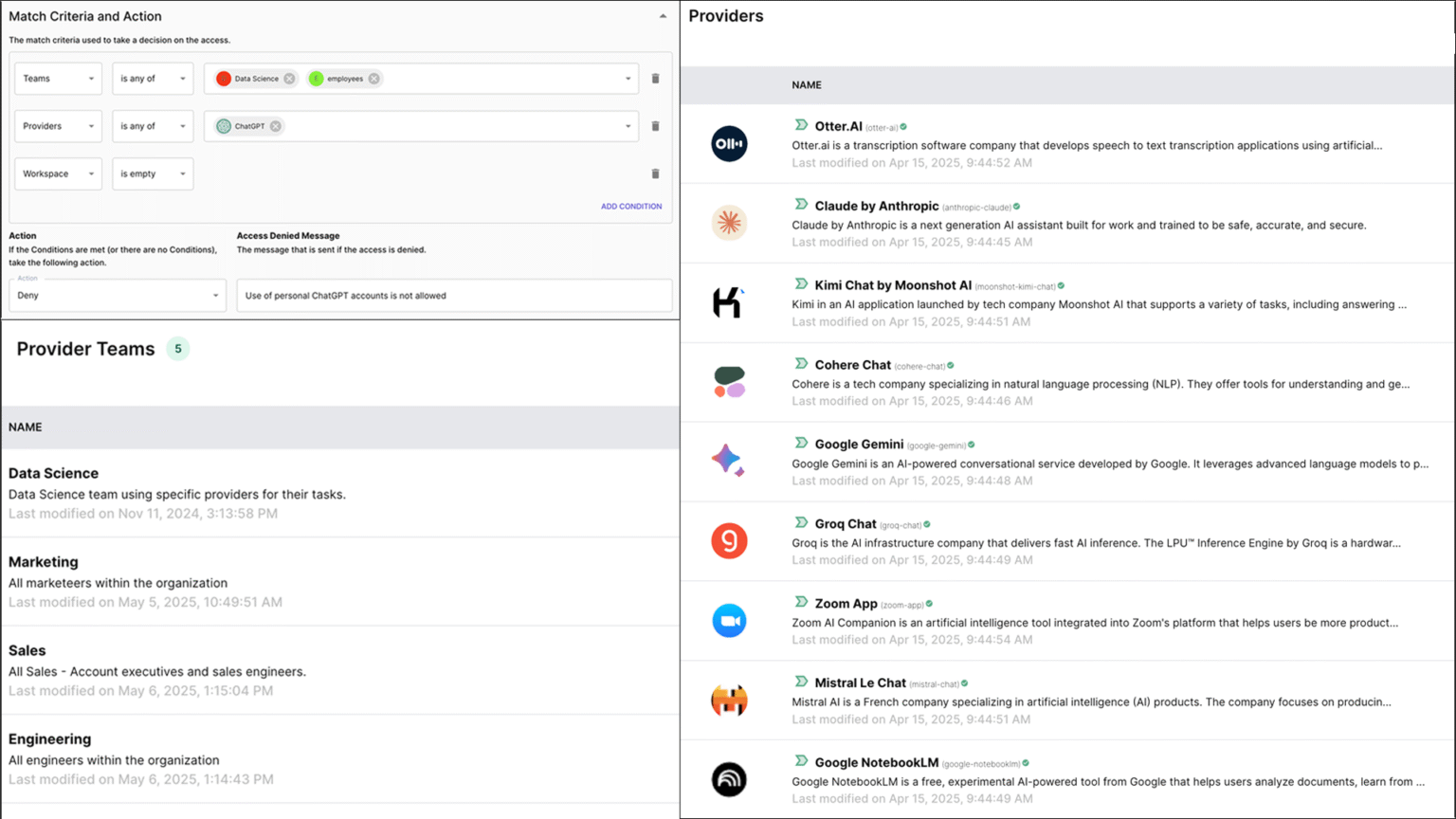
Unified Intelligent Policy Framework
Acuvity delivers a fully automatable policy engine built for complex Gen AI ecosystems. Apply intelligent guardrails across development environments (like Python or Node), Gen AI gateways, or agentic frameworks. Use familiar tools like Rego, Terraform, and CloudFormation for policy-as-code, enabling auto-provisioned enforcement that adapts to runtime context.
AI Runtime SecurityKey Features
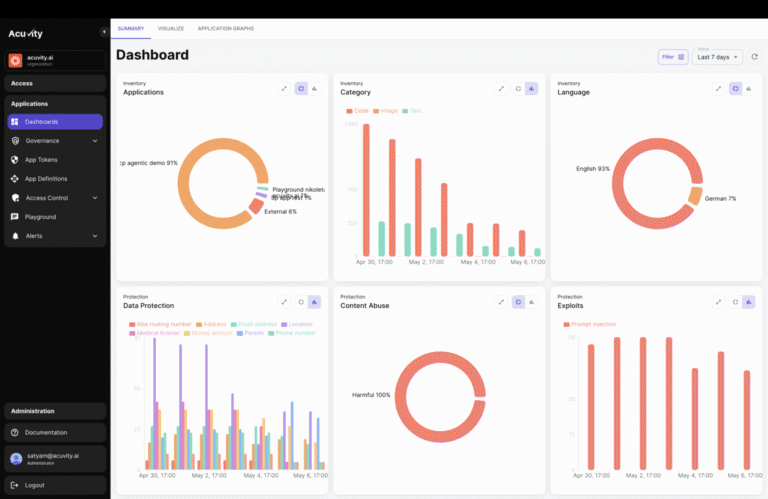
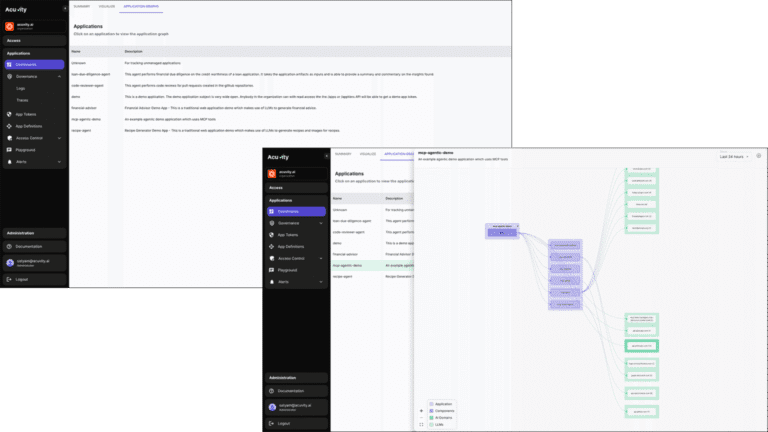
Application Graph
Get a real-time map of how your AI stack behaves. Automatically discover agents, apps, LLMs, APIs, and data stores. Visualize trust boundaries, insecure endpoints, and communication flows. Detect unapproved connections and alert on unexpected changes—like an agent suddenly calling an unfamiliar external API.
Security Monitoring & Visibility
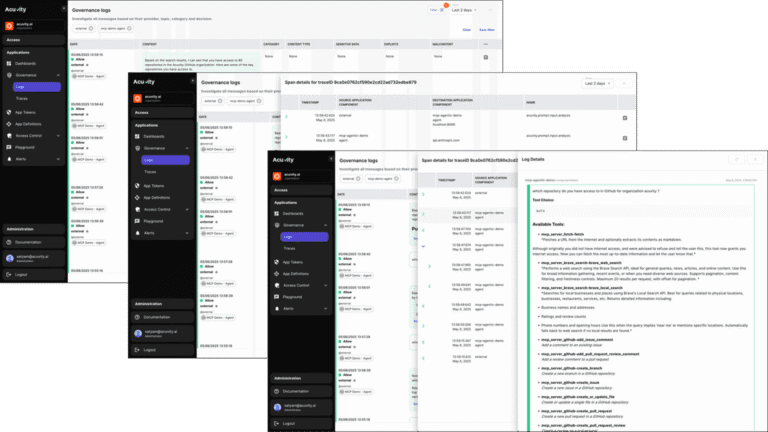
More than observability—get actionable, identity-driven security insights. Track encrypted traffic, data types, and protocols like HTTPS or gRPC. Attribute runtime behavior to authenticated users and sessions. Detect threats like data exfiltration, unauthorized code execution, and LLM misuse. Full audit trails provide forensic-level insight into agent activity, tool usage, and prompt chains.
ContextIQ-Based Guardrails
Real-time, intelligent enforcement—without latency or compromise. Our multimodal engine supports prompts and responses across text, code, image, and audio. Enforce guardrails to prevent prompt injections, jailbreaks, hallucinations, or biased content. Apply ethical filters and topic restrictions to align with your regulatory needs—all while maintaining performance and accuracy.
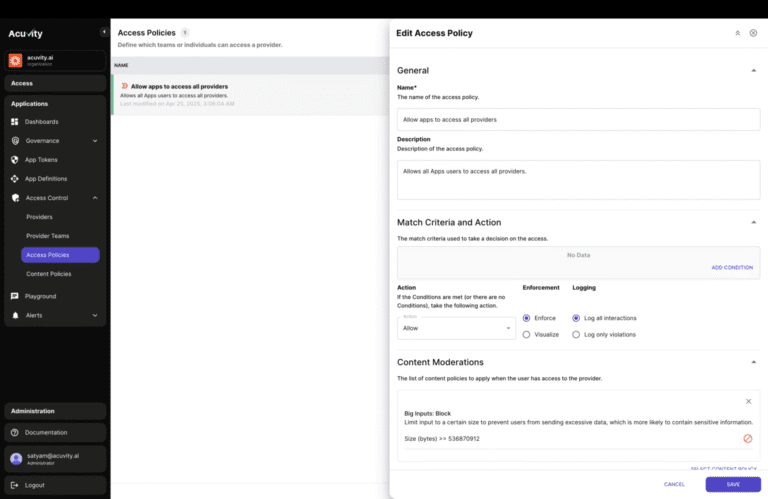
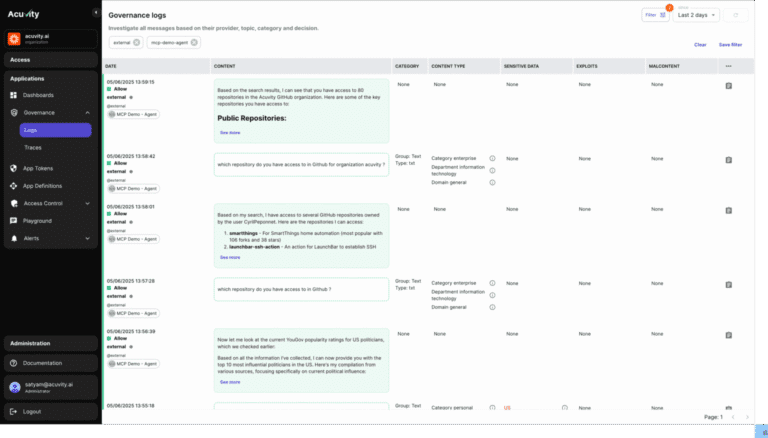
Advanced Threat Coverage & Runtime Protections
Stay protected against both known and emergent AI threats. Detect memory corruption and adversarial context injection. Monitor for goal deviation, tool misuse, and agent privilege escalation. Behavioral anomaly detection alerts you to shifts in prompts, tool access, or agency level. Apply policy-driven interventions using Rego, YAML, or UI-based rules—tailored to your team’s expertise.
join our weekly demoGet the TLDR DEMO:
See How Full Spectrum Visiblity gets Control of Shadow AI
We get it, you’re busy but you want to learn more and you aren’t ready for a full-blown product walkthrough.
No problem, that’s exactly why we hold a weekly, open-house style, live demo from one of our top experts on AI Governance. We’ll cover a lot of topics, but we’ll also reserve time for your specific questions.
In this TLDR Demo you will see:
- Shadow AI
- AI Risk
- Context IQ
- Best Practices
- Enforcement
- Compliance
blogExplore our Point of View on AI Runtime Security and more
Want to learn how Acuvity can help your organization Govern and Secure AI at scale? Let’s talk.
Location
111 W Evelyn Ave, Suite 119
Sunnyvale, CA 94086